Fraud - Prevention, Detection, and Deterrence
Omne trium perfectum is a Latin phrase conveying a simple overarching philosophy that everything that comes in threes is perfect. The rule of three in storytelling explains that people better understand concepts, situations, and ideas when they are in groups of three. Engineers and architects tell us that triangles are the strongest of all shapes. While the topic of this issue is Fraud, the theme has to be the number “three.” We don’t need to look far to see the importance of “three” for UCSF as Health, FAS, and Audit & Advisory Service (A&AS) have chosen a pyramid or triangle to illustrate our mission and stress that financial strength and stewardship are blocks upon which our true north goal sits.
However, the rule of three doesn’t always have a positive result - auditors refer to the fraud triangle to describe the effect that the coming- together of the forces of Financial Pressure, Rationalization and Perceived Opportunity have on an individual to describe the conditions leading to fraud.

Several of the case studies presented below illustrate in real terms what can happen when these forces meet: People who are under financial pressure can rationalize fraud or theft and make it a repeated behavior over years when they think there are a lack of controls in place to catch them. While we may not be able to prevent financial pressures from affecting the lives of our co-workers or issues that might trigger their rationalization, proper controls in our business processes should be able to prevent, detect, and deter fraud and remove that perceived opportunity.
Additionally, the three lines of defense model provides guidance for effective risk management and governance. Each of these lines, the Governing Body, Management, and Internal Audit, plays an important role with our control environment guarding against the risks, like fraud, that arise from our normal business processes. This model illustrates the working relationships between those three lines of defense:
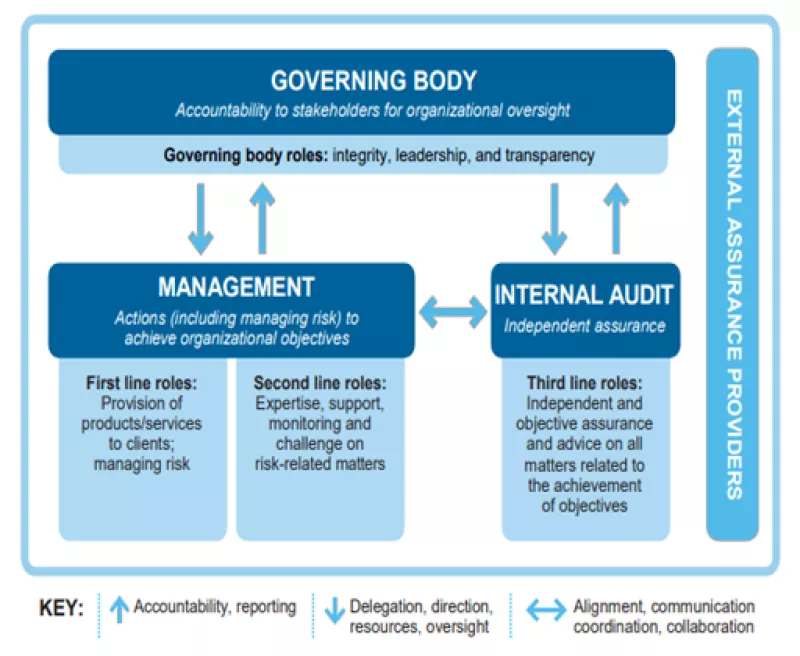
Finally, UCSF’s message on fraud should be the same at all three levels of our institution: leadership, middle management, and those on the front lines as we address this risk together. Within A&AS we are committed to fighting fraud through these three initiatives:
- Training: We host several webinars each year on different fraud-related topics. Links to our prior webinars can be found on our Fraud website (Fraudprevention.ucsf.edu). This year, we are offering small group trainings suited to the specific needs of our clients based on the fraud schemes that office might experience. For more information on setting up a training that might benefit your office contact [email protected].
- Data Analytics: Leveraging UCSF’s data to identify potential fraud and risk areas.
- Investigations: We also investigate allegations of fraud and identify any control failures that contributed to it. You may report fraud directly to [email protected] or to [email protected] or anonymously to the UC Whistleblower Hotline 1-800-403-4744 or www.ucop.edu/uc-whistleblower/index
You can have all the right strategies in the world; if you don't have the right culture, you're dead.
Patrick Whitesell
Question & Answer with Senior Vice Chancellor for Finance and Administration Erin Gore
As the senior leader at UCSF with the ultimate responsibility and oversight for campus finances and administration, and over 20 years of experience in the academic and corporate business world, who better than Erin Gore to share her insights and experiences concerning fraud and what she has learned over the years. We were excited to sit down with her to discuss this important topic.
Q: When you hear (or read) about fraud cases, what goes through your mind?
A: Fraud is such a broad topic. There are individuals who try to put their interests before those of UCSF, the government, and our community, working around the clock to come up with ways to “scam” UCSF. I worry about this a lot. I think about how each of us should be the first line of defense against fraud without making it painful for our researchers, faculty, and community. We need to use our available resources and controls to pro-actively look for fraud. This doesn’t mean having multiple internal approvers – because, in reality, the more approvers, the less accountability any individual takes on. We need to continue to have people who diligently think about fraud, look for patterns of abuse, and, if there are red flags, they will take a deep dive into what they see.
Q: As SVC for Finance & Administration at UCSF, what is your biggest fear in regard to fraud?
A: I am always concerned about the power dynamics between those whose job is to review expenses or provide higher-level direction if they receive pushback when they question the actions of those doing incredible scientific work yet may also be intentionally or unintentionally committing fraud. It can be difficult to stand up to this kind of resistance; I think it is really important that we, as an institution, support the efforts of our people whose job it is to investigate and fight fraud, wherever and whenever it might occur.
Q: At Wells Fargo or any of your prior jobs, did you ever experience fraud and what did you learn from that/those experience/experiences?
A: It feels like every year I learn about some fraud that was just uncovered. By nature, I believe everyone comes to work trying to “do the right thing,” but unfortunately, that is not always the case. I have learned that we need systems and reporting tools to help us see patterns of potential fraud. We need to ensure we have enough space for our managers to look at all areas they are responsible for and identify behavior patterns across grants or funding sources that may indicate fraud. Lastly, we need to discuss what organizational and system configurations are needed to help support the efforts of those whose job is to look for and investigate fraud.
Fraud in the News
We scoured the news outlets to bring you real-life stories about fraud occurring at colleges and universities around the U.S. that you might find interesting to your work here at UCSF.
Fraud at Bay Area Universities Tied to Overseas Criminal Organization
In separate federal indictments linked to the same conspiracy, FBI arrested employees at Cal and Stanford after investigation revealed that for several years they stole laptops and computers they had fraudulently ordered. Key takeaways from this case include the below methods and control gaps.
- Both were able to generate purchases of identical laptops from a single request, simultaneously, using different procurement methods at the same time.
- One laptop was given to the requester, who accepted receipt, while the second (the fraudulently purchased laptop) was sold and shipped to criminals overseas.
- A single receipt was used to clear both transactions and, because the laptops were the same make/model, individual transactions seemed legitimate. The fraud was not detected until review of all procurement methods occurred.
- Both criminals took advantage of situations where each procurement method had different approvers and the systems did not communicate data.
- One also exploited a situation where their supervisor, who normally reviewed P-Card transactions, had retired and was not replaced.
To avoid this scenario occurring at UCSF, here are a few steps to take.
- Departments are encouraged to review purchases across every purchasing method and all chart strings available to their employees.
- If the number of laptops purchased by a person far exceeded that of others, departments should compare purchasing patterns of employees in similar roles and question outliers.
- Departments need to make sure vacated roles/responsibilities are quickly filled to ensure segregation of duties after retirements, extended leave, or reorganizations.
https://www.nytimes.com/2022/04/20/us/stanford-laptops-theft.html
Manipulating the Threshold
A Yale School of Medicine employee was sentenced to 9 years after being convicted in a $40 million fraud scheme. Over 12 years, the employee abused her position as a Finance Director to initiate her own purchases, or approve purchases of direct reports, for thousands of laptop computers. In 2021 alone she purchased 8,000 iPads and Surface Pros purportedly for research studies. This scheme involved the fraudulent use of Purchase Orders submitted in amounts slightly under the approval limit of $10,000 set for her role. The money generated from the fraud was used to purchase luxury cars, real estate and finance a lavish lifestyle.
This scheme illustrates a common behavior of fraudsters who target dollar amounts just below policy thresholds set for additional review. Important limits at UCSF to remember:
- $500 purchases in BearBuy do not need initial approval.
- $5000 in BearBuy for employees with self-approving roles.
- $10,000 in BearBuy necessitates approval by a Supply Chain Management Buyer.
- At each of these levels, even if total spend is not over budget, review must include close scrutiny for personal items, often hidden as “split” purchases in amounts just below these thresholds, made on the same or consecutive days.
- As approvers of transactions in BearBuy, P-Cards and MyExpense are often different, Supervisors need oversight of purchases made by direct reports across all of these procurement methods.
This scenario also shows how a simple monthly or quarterly data review would have detected excessive purchasing patterns or outliers by an individual or department.
Financial Pressures Can Create Hidden Fraud Gems
A Penn State employee who defrauded the public during a decade-long scheme was sentenced to a year in federal prison. The employee misused a P-Card to purchase $267,000 worth of computer equipment purportedly needed to upgrade, replace, or maintain servers and resold it to other criminals. This theft was hidden in larger, legitimate purchases.
At sentencing, the judge and prosecutor noted, “Each purchase and sale involved dozens of deliberate steps…a willingness to engage in each of these steps throughout this long-running fraud exhibits a comfort in his own criminality…. This was not a simple lapse in judgment.” The defense sited the employee’s low salary, combined with familial problems and serious financial difficulties as mitigation for the conduct.
This story sadly illustrates the “Fraud Triangle” (see above) which states, “when the combined force of financial need, perceived opportunity and rationalization exist a person is highly likely to pursue fraudulent activities.”
Departments should remember the following controls and monitor for compliance:
- P-Cards are for low-value items only and the preferred procurement method for computer equipment is BearBuy.
- Data analytics used to review purchases will call attention to high volume/dollar purchases and patterns inconsistent with someone’s role.
- Segregation of duties: those who order equipment should not receive it or maintain the inventory records.
- Inventory records should be maintained and periodically checked to ensure that what was ordered is present.
- Excessive/unexplained wealth by staff is a red flag for possible fraud.
Professor Arrested After Theft of Travel Reimbursement Funds
A 30 year faculty member of Utah State University was arrested after an internal audit (hurray for internal audit) revealed he filed false travel reimbursements. Auditors discovered 24 trips occurring over a five-year period in which he claimed reimbursement of mileage on his personal car when he had actually used a university vehicle. The audit also showed 10 trips in which he inappropriately claimed extra per diem and/or lodging and that he also included meals that did not qualify for reimbursement. On one occasion, he actually attended his daughter’s wedding, paid for the family’s Airbnb rental, then used white-out on the receipt before submitting it for reimbursement.
Helpful hints for MyExpense reviewers to keep in mind for travel expenses:
- Altered receipts, missing receipts and receipts ending in whole dollar amounts are all red flags for fraud.
- Fraudsters who rode with co-workers will claim use of their own vehicle or say they departed from an address farther away from their residence in an attempt to increase mileage and toll reimbursement.

